Welcome to the Smart Service Rootkit Removal Guide, your ultimate solution to safeguarding your digital world against insidious cyber threats. Dive into this comprehensive article as we unveil effective techniques and expert tips to rid your devices of this cunning malware. Brace yourself for a transformative journey towards a smart, secure, and worry-free online experience.
Recently, Fortect has become increasingly popular as a reliable and efficient way to address a wide range of PC issues. It's particularly favored for its user-friendly approach to diagnosing and fixing problems that can hinder a computer's performance, from system errors and malware to registry issues.
- Download and Install: Download Fortect from its official website by clicking here, and install it on your PC.
- Run a Scan and Review Results: Launch Fortect, conduct a system scan to identify issues, and review the scan results which detail the problems affecting your PC's performance.
- Repair and Optimize: Use Fortect's repair feature to fix the identified issues. For comprehensive repair options, consider subscribing to a premium plan. After repairing, the tool also aids in optimizing your PC for improved performance.
Understanding Rootkits
Rootkits are a type of malicious software that can infiltrate your computer and hide their presence, making them difficult to detect and remove. If you suspect that your device may be infected with a rootkit, follow these steps to remove it:
1. Start by booting your computer in Safe Mode. To do this, restart your PC and press the F8 key repeatedly until the Advanced Boot Options menu appears. Use the arrow keys to select “Safe Mode” and press Enter.
2. Once in Safe Mode, open the Command Prompt by typing “cmd” in the search bar and selecting the result.
3. In the Command Prompt, run a rootkit scanner such as Malwarebytes Anti-Rootkit Scanner or Comodo Cleaning Essentials. These programs will scan your system for any rootkit infections.
4. After the scan is complete, follow the instructions provided by the scanner to remove any detected rootkits.
5. Additionally, you can perform a virus scan using a reputable antivirus program like Malwarebytes Premium to ensure your system is free from any other malware.
How Rootkits Work
Rootkits can be tricky to remove, but with the right tools and steps, you can effectively get rid of them on your Windows device.
1. Start by booting your PC into the System Recovery Options or Advanced Boot Options. You can do this by pressing the F8 key repeatedly during startup or using an installation disc or repair disc.
2. Once you’re in the recovery options, select Repair your computer or Startup Options, depending on your version of Windows.
3. Choose your language settings and click Next. Then, enter your username and password if prompted.
4. In the recovery options menu, select Command Prompt.
5. Use a reliable rootkit removal tool like Malwarebytes Anti-Rootkit Scanner, Comodo Cleaning Essentials, or Malwarebytes Premium to scan and remove the rootkit from your system.
6. Follow the instructions provided by the chosen tool to complete the rootkit removal process.
Remember, it’s essential to regularly scan your system for rootkits and other malware to ensure your device’s security.
Signs of a Rootkit Attack
- Step 1: Identify unusual computer behavior
- Monitor for unexpected crashes, freezes, or slowdowns
- Keep an eye out for strange error messages or pop-ups
- Take note of any unexplained network activity
- Step 2: Perform a thorough antivirus scan
- Open your preferred antivirus software
- Update the virus definitions to ensure the latest protection
- Initiate a full system scan
- Quarantine or remove any identified threats
- Step 3: Use a reputable anti-rootkit tool
- Research and select a reliable anti-rootkit tool
- Download and install the chosen anti-rootkit software
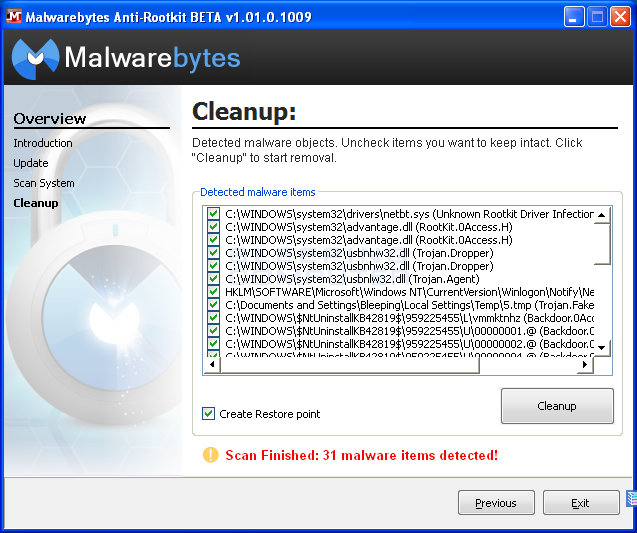
- Update the tool to its latest version
- Run a deep scan of your system using the anti-rootkit tool
- Follow the tool’s instructions to remove any detected rootkits
- Step 4: Update your operating system and software
- Check for available updates for your operating system
- Install all critical updates and patches
- Update all installed software to the latest versions
- Regularly enable automatic updates to stay protected
- Step 5: Strengthen your security measures
- Install a reliable firewall to monitor network traffic
- Enable real-time scanning and behavior-based detection in your antivirus software
- Consider using a reputable anti-malware program in addition to antivirus software
- Regularly back up your important files and data

Detecting and Identifying Rootkits
- Perform a Full System Scan
- Open the Antivirus Software installed on your computer.
- Click on the option to run a full system scan.
- Allow the antivirus to thoroughly scan all files and directories on your computer.
- Make note of any suspicious files or activities detected during the scan.
- Monitor System Performance
- Pay attention to any unusual behavior or slowdowns in your computer.
- Look for signs such as excessive CPU or memory usage.

- Check the Task Manager to identify any suspicious processes running in the background.
- Take note of any unfamiliar or suspicious programs or services.
- Check for Unusual Network Activity
- Open the Network Activity Monitor or a similar network monitoring tool.
- Look for any excessive or unusual network traffic.
- Identify any suspicious connections or unknown IP addresses.
- Check for any unauthorized data transfers or communication.
- Inspect System Files and Registry
- Open the Command Prompt as an administrator.
- Run the command sfc /scannow to scan and repair system files.
- Check for any modified or corrupted system files.
- Inspect the Windows Registry for any suspicious or unauthorized entries.
- Use Rootkit Detection Tools
- Download and install a reputable rootkit detection tool.
- Run a scan using the tool to identify any hidden rootkit components.

- Follow the tool’s instructions to remove or quarantine any detected rootkits.
Types of Rootkits
- Kernel rootkits: These rootkits target the core of the operating system, known as the kernel, making them extremely difficult to detect and remove.
- Bootloader rootkits: Bootloader rootkits infect the system’s bootloader, which is responsible for loading the operating system. They execute even before the operating system starts, giving them deep control over the system.
- Memory rootkits: Memory rootkits reside in the system’s memory, making them invisible to traditional antivirus software. They can modify the running processes and hide their presence effectively.
- Application rootkits: Application rootkits target specific software applications, exploiting vulnerabilities to gain control over them. They often manipulate their behavior and evade detection.
- Firmware rootkits: Firmware rootkits infect the firmware of devices, such as routers or hard drives. They can persist even after reformatting the device’s storage, making them challenging to remove.
- Virtual rootkits: Virtual rootkits operate within virtual environments, such as virtual machines or hypervisors. They can compromise the security of multiple virtual instances simultaneously.
Steps to Remove a Rootkit
1. Start by booting your computer from an installation disc or a system repair disc. Press any key to boot from the disc when prompted.
2. Select your keyboard language settings and click “Next”.
3. Choose “Repair your computer” and then select “Troubleshoot” followed by “Advanced options”.
4. From the “Advanced options” menu, select “Startup Options” and click “Restart”.
5. When your computer restarts, choose “Safe Mode with Networking” using the arrow keys and press “Enter”.
6. Once in Safe Mode, open your web browser and download the Malwarebytes Anti-Rootkit scanner.
7. Install and run the scanner, following the on-screen instructions.
8. Perform a rootkit scan using the scanner to detect and remove any rootkit malware.
9. After the scan is complete, restart your computer normally and run a full virus scan using reputable antivirus software like Malwarebytes.
10. If any infected files are found, follow the software’s prompts to remove them.
Preventing Rootkit Attacks
To protect your system from rootkit attacks, follow these steps:
1. Start by disconnecting your computer from the internet to prevent further access by hackers.
2. Restart your computer and enter System Recovery Options by pressing F8 during startup.
3. Choose “Safe Mode with Networking” to load Windows with basic services and network support.
4. Download and install a reputable anti-malware software bundle such as Malwarebytes Anti-Rootkit Scanner.
5. Run a full rootkit scan using the software to detect and remove any rootkit malware.
6. If the scan finds any threats, follow the software’s instructions to quarantine or remove them.
7. Restart your computer in normal mode and check for any remaining issues or symptoms.
8. Keep your operating system and antivirus software up to date to prevent future attacks.
9. Be cautious when clicking on links or downloading files from unknown sources.
10. Regularly backup your important data to avoid data loss in case of an attack.
Examples of Rootkits
Smart Service Rootkit Removal Guide
| Rootkit Name | Description | Impact |
|---|---|---|
| Alureon | Alureon is a sophisticated rootkit that targets Windows operating systems. It is known for its ability to hide itself and other malware, making it challenging to detect and remove. | Alureon can steal sensitive information, modify system files, and create backdoors for remote access. |
| Zeus | Zeus, also known as Zbot, is a well-known rootkit that primarily targets financial institutions. It is often distributed through phishing emails and exploit kits. | Zeus can log keystrokes, capture login credentials, and perform unauthorized transactions, leading to financial loss. |
| TDL | TDL (TDSS) is a highly persistent rootkit that infects Windows systems. It uses advanced techniques to evade detection and removal, making it a significant threat. | TDL can download and install additional malware, conduct click fraud, and participate in botnet activities. |
| Stuxnet | Stuxnet is a complex rootkit that gained notoriety for its role in sabotaging Iran’s nuclear program. It specifically targets industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. | Stuxnet can cause physical damage to critical infrastructure, disrupt operations, and compromise sensitive data. |
| Rustock | Rustock is a rootkit that primarily operates as a spam botnet. It infects Windows systems and turns them into spam-sending machines without the user’s knowledge. | Rustock can send massive amounts of spam emails, overload email servers, and contribute to the spread of malicious content. |
Protecting Your Devices with Anti-Rootkit Software
Protect Your Devices with Anti-Rootkit Software
Protecting your devices from rootkit viruses is crucial to safeguarding your privacy and security. Rootkits are malicious software that can hide deep within your device’s operating system, making it difficult to detect and remove them. To ensure your device stays secure, it’s important to use reliable anti-rootkit software.
One effective solution is the Malwarebytes Anti-Rootkit Scanner. This software is designed to detect and remove rootkits, keeping your device safe from potential threats. Here’s how you can use it to protect your device:
1. Start by downloading and installing the Malwarebytes Anti-Rootkit Scanner from their official website.
2. Once installed, open the software and click on “Scan” to initiate a thorough scan of your device.
3. The scanner will then search for any rootkit viruses or suspicious files on your device.
4. Once the scan is complete, the software will display a list of detected threats. Click on “Remove” to eliminate them from your device.
Remember to regularly update your anti-rootkit software to stay protected against the latest threats. By taking these proactive measures, you can ensure the safety and security of your devices.
Best Practices for Rootkit Prevention
1. Keep your operating system (e.g., Windows 10) and software bundle up to date to prevent vulnerabilities that hackers can exploit.
2. Avoid downloading suspicious files or clicking on unknown links, as they may contain malware or rootkit viruses.
3. Use strong and unique passwords for all your accounts, including your Windows login.
4. Regularly scan your system using reputable anti-malware software like Malwarebytes Anti-Rootkit Scanner or Malwarebytes, which can detect and remove rootkit viruses.
5. Be cautious when granting administrative privileges and only give them to trusted applications or users.
6. Consider creating a system repair disc or USB drive that can help you recover your system in case of a rootkit infection.
7. Enable Windows notifications and regularly check for any unusual or unexpected activity.
Remember, prevention is key when dealing with rootkits. Stay vigilant and take proactive measures to protect your system from potential threats.